AWS Identity and Access Management (IAM) is a fundamental web service that helps you securely control access to your AWS resources. It acts as the central control point for managing who (authentication) can do what (authorization) within your AWS account.
Why is IAM Important?
- Security: Prevents unauthorized access and actions.
- Granular Control: Define specific permissions (Principle of Least Privilege).
- Centralized Management: Manage users, groups, roles, and policies in one place.
- Secure Access: Avoid sharing root account credentials; use IAM users and roles instead.
- Compliance: Helps meet security and regulatory requirements.
Core IAM Components: Definitions
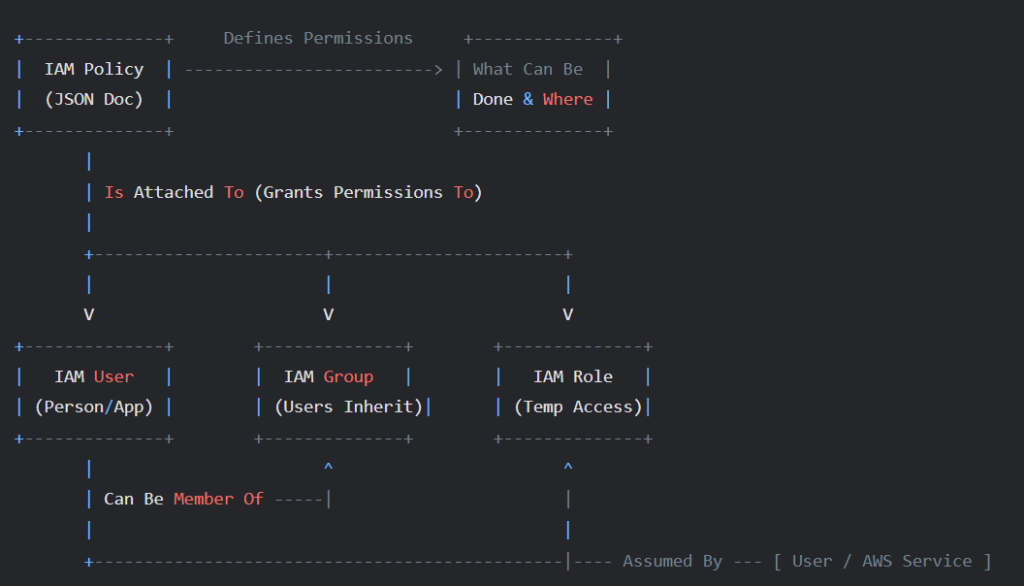
- IAM User:
- An entity (person or application) that interacts with AWS.
- Has long-term credentials:
- Username/Password (for Console access)
- Access Key ID & Secret Access Key (for programmatic access – CLI, SDKs)
- Analogy: An individual employee’s ID badge.
_____________________________________________________________
- IAM Group:
- A collection of IAM Users.
- Users within a group inherit the permissions assigned to that group.
- Simplifies permission management for multiple users.
- Analogy: A department (e.g., “Developers”, “Testers”).
- IAM Policy:
- A JSON document that defines permissions (what actions are allowed or denied on which resources).
- Key elements: Effect (Allow/Deny), Action (API calls like s3:GetObject), Resource (AWS resources like a specific S3 bucket ARN), Condition (optional constraints).
- Can be AWS Managed (pre-defined) or Customer Managed (you create).
- Analogy: The rulebook or access control list.
- IAM Role:
- An identity that AWS resources, services, or external users can assume temporarily.
- Does not have long-term credentials like users.
- Provides temporary security credentials upon assumption.
- Crucial for granting permissions to AWS services (e.g., Lambda accessing DynamoDB) or enabling cross-account access.
- Defined by a Trust Policy (who can assume it) and Permissions Policies (what the role can do).
- Analogy: A specific job hat (e.g., “Database Updater”) granting temporary powers.
Component Relationships
These components work together to manage access:
- Policies are attached to Users, Groups, or Roles to grant permissions.
- Users can belong to one or more Groups.
- A User’s permissions are the sum of policies attached directly to the user and policies attached to any Groups they are in.
- An IAM Role gets its permissions only from the policies attached directly to it.
- Entities (like Users, other AWS Services, Federated Identities) assume a Role to gain its permissions temporarily, shedding their original permissions during that session.
Real-World Use Case: Serverless Web App
Scenario: A web application backend using:
- API Gateway: Receives user requests.
- AWS Lambda: Executes business logic.
- DynamoDB: Stores application data.
IAM Requirement: The Lambda function needs permission to:
- Read/Write data in the specific DynamoDB table.
- Write logs to CloudWatch Logs for monitoring/debugging .
IAM Solution:
- Create an IAM Policy granting the necessary dynamodb:* actions (e.g., GetItem, PutItem) on the specific DynamoDB table ARN and logs:* actions (e.g., CreateLogStream, PutLogEvents) for CloudWatch Logs.
- Create an IAM Role (often called an “Execution Role”) with a Trust Policy allowing the Lambda service (lambda.amazonaws.com) to assume it.
- Attach the Permissions Policy (from step 1) to the Role (from step 2).
- Assign this Role to the Lambda function during its creation or configuration.
Benefit: The Lambda function automatically obtains temporary credentials via the Role, securely accessing DynamoDB and CloudWatch without needing hardcoded Access Keys.
AWS CLI Commands for Lambda Execution Role
These commands create the IAM resources for the Lambda function in our example.
(Ensure AWS CLI is installed and configured: aws configure)
1. Create the Permissions Policy Document:
Save the following JSON content as lambda-dynamodb-policy.json.
IMPORTANT: Replace placeholders YOUR_REGION, YOUR_ACCOUNT_ID, and YourTableName with your actual values!
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowDynamoDBAccess",
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:PutItem",
"dynamodb:UpdateItem",
"dynamodb:DeleteItem",
"dynamodb:Query",
"dynamodb:Scan"
],
"Resource": "arn:aws:dynamodb:YOUR_REGION:YOUR_ACCOUNT_ID:table/YourTableName"
},
{
"Sid": "AllowCloudWatchLogs",
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:*:*:*"
}
]
}2. Create the IAM Policy:
Creates the policy in AWS from the JSON file. Note the output Policy ARN.
aws iam create-policy --policy-name LambdaDynamoDBAccessPolicy --policy-document file://lambda-dynamodb-policy.json3. Create the Role Trust Policy Document:
Save the following JSON content as lambda-trust-policy.json. This allows the Lambda service to assume the role.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "lambda.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}4. Create the IAM Role:
Creates the role container using the trust policy.
aws iam create-role --role-name LambdaDynamoDBExecutionRole --assume-role-policy-document file://lambda-trust-policy.json5. Attach the Policy to the Role:
Connects the permissions policy (created in step 2) to the role (created in step 4). Replace YOUR_POLICY_ARN with the actual ARN from the create-policy output.
aws iam attach-role-policy --role-name LambdaDynamoDBExecutionRole --policy-arn YOUR_POLICY_ARNKey IAM Best Practices
- Principle of Least Privilege: Grant only the minimum permissions required to perform a task. Avoid overly permissive policies (like *:*).
- Avoid Root User: Do not use your root account for everyday tasks. Create IAM users with specific permissions.
- Use Roles for Applications & Services: Prefer IAM Roles over embedding long-term Access Keys in applications running on AWS (e.g., EC2, Lambda, ECS).
- Enable Multi-Factor Authentication (MFA): Add an extra layer of security, especially for the root user and privileged IAM users.
- Use Groups for Users: Manage permissions efficiently by assigning policies to groups rather than individual users where possible.
- Regularly Audit Permissions: Use tools like IAM Access Analyzer and review policies periodically to remove unnecessary access.
- Use Policy Conditions: Further restrict access based on factors like source IP address, time of day, or MFA status.
Conclusion
Understanding and correctly implementing AWS IAM is crucial for building secure, scalable, and well-managed applications in the AWS cloud. By using Users, Groups, Roles, and Policies effectively, you gain fine-grained control over your resources.
For the full explanation and demonstration, please refer back to the YouTube tutorial.
